Holistic Zero Trust security for distributed and hybrid environments
PROTECT IOT INFRASTRUCTURE
Our Cyber Security Architecture
We appreciate the diversity of distributed architecture, which most often is seen as an enterprise's key note differentiator. With this diversity, Enterprise Risk Management clearly takes precedence while ensuring threat-free cyber operations.
The most effective cybersecurity service must have all functions communicate effectively to take informed decisions on risk acceptance, measuring analogies in real time and deliver a Zero Trust environment for broad user communities, leveraging Software Defined Perimeters.
We ensures the highest level of cybersecurity by mapping our solution to your expanding perimeter, rendering digital verification, securing gaps in data exchange and offering core security of data and other precious assets that just cant be compromised. Take a confident next step with our redefined cybersecurity cloud today!
Benefits


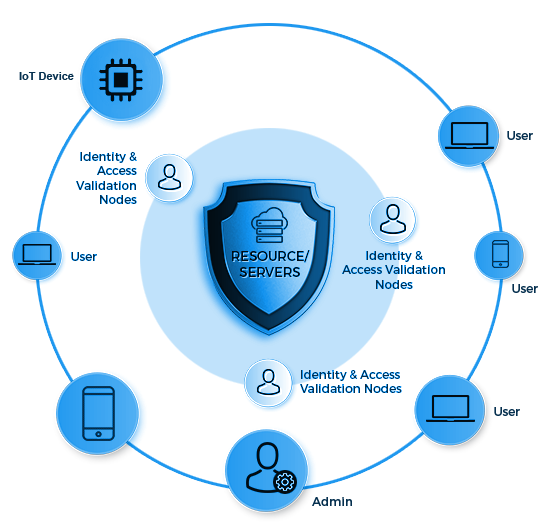
Access to the network and systems granted only to authorized users and devices

Authentication and controlled access is based on digital id’s

Prevents the spread of malware and ransomware in unpatched/ hardened systems

Easy deployment, minimal changes to existing environment

Secure anytime anywhere access to mobile workforce
Deployment Architecture
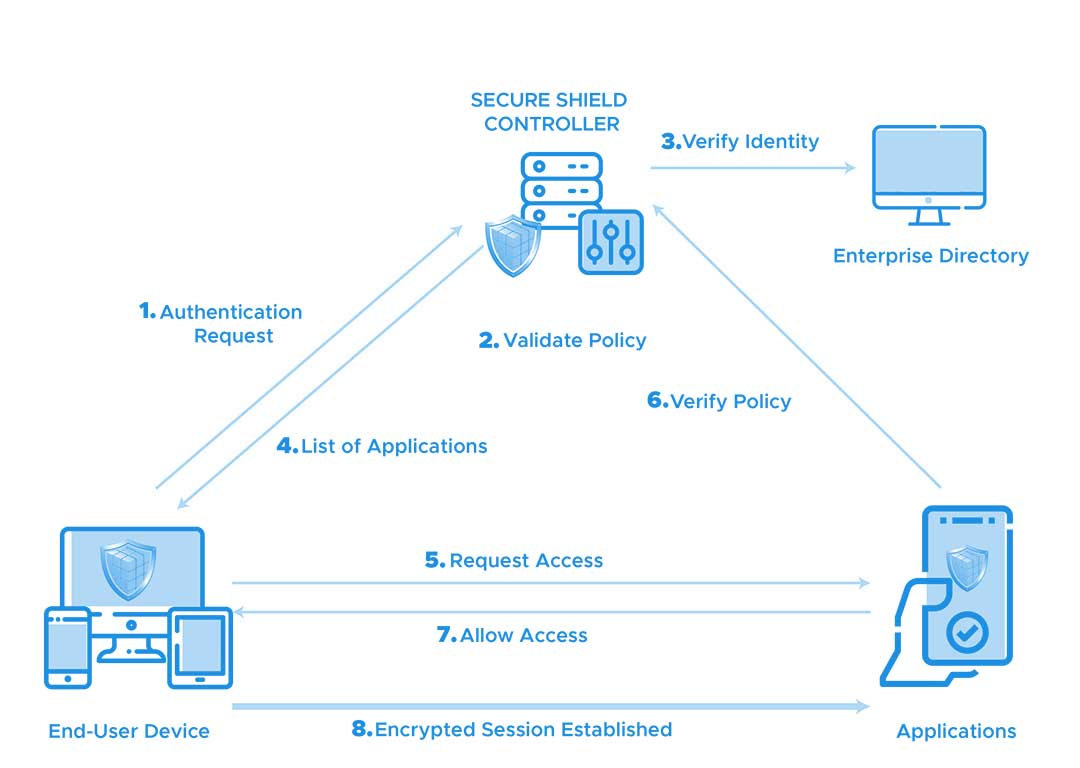
Secure shield provides Unified Secure Access from anywhere to anywhere- Remote as well as local users, data center as well as cloud applications, all using a single platform
IOT Armour
A next-gen military-grade security system to protect critical infrastructure and connected devices in the Internet of Things Smarter, faster and ready to scale for tomorrow’s networks

Cryptographically secure digital identity
for users, connected devices and central servers/ services

Invisible & locked down critical systems
with micro-segmentation and fine-grain access control

Best-in-class military-grade encryption
For secured access to connected devices and IoT communication

Immutable & tamper-proof logs
stored securely on the Blockchain for instant access/ analysis
IoT Security: A growing challenge
The Internet of Things connects numerous everyday devices, opening up previously closed systems to remote access & control. Smart, connected devices are now an integral part of our lives, in business and at home. Be it Smart Cities with sensors and digital management systems for energy, utilities, transportation, etc, or smart homes and offices with a host of connected and smart devices, connected cars, UAVs or even Industrial control systems.
Building Blocks

Blockchain Technology
- Decentralization
- Cryptographic encryption
- Immutability
- Consensus-based control

Software Defined Perimeter (SDP)
- Render devices invisible to attackers
- Military grade architecture
- Developed at the Defense Information Systems Agency (DISA)

IOT Agent Tech
- Quick customization
- Fortification & invisibility
- Nano-client
- Two factor authentication

Transport Layer Security (TLS)
- A cryptographic protocol
- Privacy and security during communication over a network
- Public and private key encryption
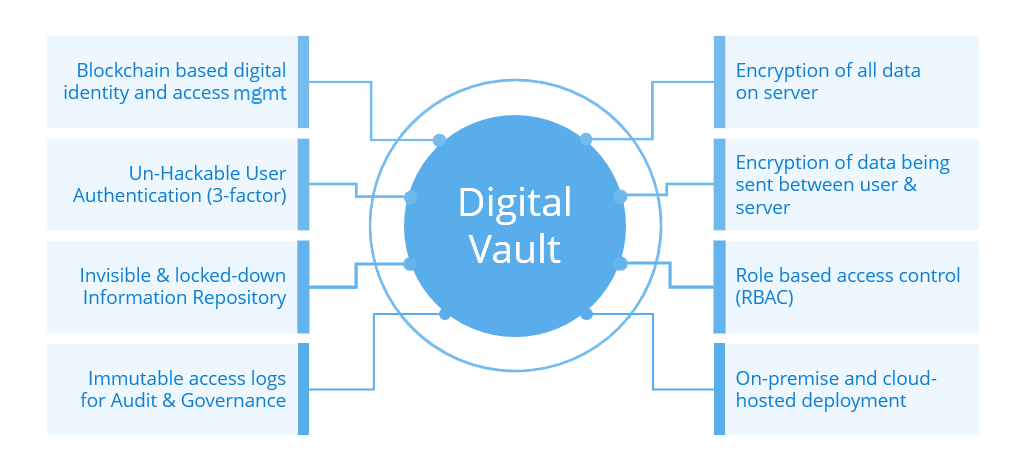
Digital Vault Features
The Result
Maximum security for your most sensitive information and instant availability wherever you need to access it.

End to End Cryptographic Encryption

Platform visible only to authorized users –Safe to host and share files on the internet

Un-hackable and simple user authentication coupled with role-based access control

Instant visibility of any illegitimate attempts to access content



